The shift to distributed work has permanently altered business processes.
Your remote work cybersecurity perimeter is no longer just a locked corporate office. It now extends to home networks, personal devices, and public Wi-Fi that your IT team can neither monitor nor control. For small and medium-sized businesses, the critical question of “how do you protect sensitive information when your team can work anywhere?” arises.
Contrary to popular belief, you do not need to add complicated enterprise solutions.
The answer is to bake security in from the start, create and administer security policies, implement the tools that make a difference, and build a culture where everyone, from engineers to Virtual Assistants, knows their role in keeping the company safe.
What is Cybersecurity for Remote Work?
Cybersecurity for remote work is the safeguarding of your organization's data, systems, and networks when your personnel work from nontraditional office environments. Unlike traditional office security, which was focused on the protection of the office building, cybersecurity for remote work supports an organization facing the unique challenges of remote work, which include:
- Your security perimeter extends to every employee's at-home network and devices.
- Company data is traversing unknown networks and the internet.
- Team members are accessing sensitive data from multiple locations and devices.
This module of operation recognizes that cybersecurity cannot reside solely in the office building; it must follow data wherever it goes and protect its employees, regardless of remote work protocols.
Why Security Must Be Built In, Not Become An Afterthought
Traditional office environments rely on controls such as managed devices, monitored networks, and physical oversight. When remote work appeared, all of these reverted overnight. Now it is possible for your people to be using personal laptops that have not been updated in 6 months, with home routers that still have the default password, and networks that may have compromised smart devices.
The human factor only increases the technical vulnerability. Phishing attacks now cast a wide net and can closely resemble executive communication, vendor invoices, and client requests. Remote workers employed on behalf of client groups, such as Virtual Assistants, are easy targets.
Shadow IT is also a risk. This happens when employees use unapproved applications because approval can take too long. What commonly happens is that sensitive customer data is transferred to employees' personal cloud profiles, which are known to your IT department. Then, the data is passed along through an unencrypted service and accessed by a contractor who was never assigned, never worked, and was never removed from access.
Periodically conducting a cloud risk assessment can help surface exactly these kinds of gaps, identifying where sensitive data has drifted outside approved environments and whether access controls still reflect the actual composition of your team.
The common denominator in all three increasing risk factors is the operational gap. Organizations do not fail at security because they are not sophisticated enough to buy the tools, but because they never had security built into the process from the beginning to the day-to-day.
Five Policies That Create Your Security Foundation
Effective policies are not forgotten in folders. They guide how work gets done every day. These five policies set clear expectations that protect both the business and its people.

Acceptable Use Policy
Establish clear parameters about what is acceptable and what is prohibited when using a company resource. The most significant issue revolves around browser extensions. Many well-known, widely used browser extensions request permission to read and modify all web pages, exposing your data. Create three separate categories: required tools, optionally approved and inventoried tools, and simply unacceptable tools, which introduce far too much risk.
Password and Secrets Management
The fact is that people cannot effectively create, remember, and manage strong, unique passwords for the many accounts they will use. Therefore, make password management a requirement rather than an option. Ensure that every credential utilized at work is generated and stored in the password manager. Furthermore, it must be secure once granted access, meaning the item itself is shared at the item level rather than via a password.
Multi-Factor Authentication
Multi-factor authentication (MFA) gives you the most value for your security investment. MFA blocks almost all account break-ins, even if someone gets a password. Make MFA required for every account that can access sensitive data, starting with email, since it is often used to reset other accounts.
Data Classification and Handling
If you are missing a clear data classification, employee behavior, concerns, and goal setting will dictate each employee's understanding of what is sensitive and how to protect it. Categorize data into four levels: Public, Internal, Confidential, and Restricted. For each classification level, provide pre-designated rules. For example, confidential data must be encrypted and tagged for limited access, while restricted items may require increased logging, limited access, and additional steps in the approval process.
Device and Least-Privilege Access
Any device that requests access to company systems and any individual who obtains permissions presents some level of risk.
The key to success here is least privilege.
Everyone should have access only to the security information and systems necessary to perform their job, nothing more. You will need to map the relevant role to the least-privilege access it must have. Also, review the permissions granted on a quarterly basis and evaluate if they remain accurate.
Five Technologies that Automate Security
Policies set expectations and create best practices while technology makes compliance a natural, rather than painful, experience.
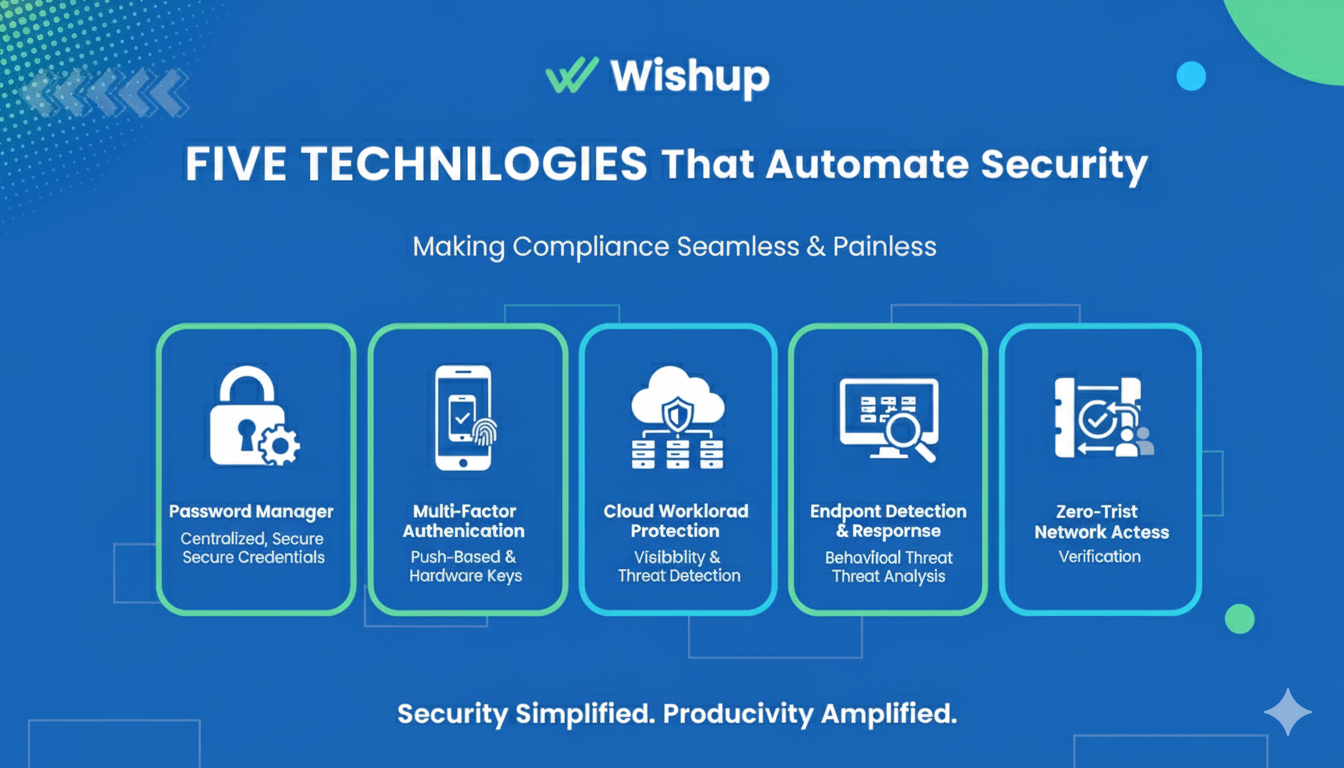
Password Manager
For Password Manager, select a business-level product with centralized management, team vault functionality for storing shared credentials, and complete audit logs. Make sure to include installation as part of your employee onboarding process on day one, where they open nothing else but the password manager before they receive access to other systems. Use the built-in security dashboard monthly to identify weak passwords and accounts that do not require Multi-Factor Authentication.
Multi-Factor Authentication Everywhere
The implementation path is clear: email first, then administrative and financial systems, and finally productivity tools used daily. For most users, multi-factor authentication via a push-based authenticator app provides very strong security while still maintaining an acceptable level of friction. For high-privilege accounts, you should require a hardware security key that provides phishing-resistant cryptographic verification.
Cloud Workload Protection
For businesses that build or run cloud applications, security is not only about user access; it is also about infrastructure and configuration. Cloud workload protection security, when done right, can give you continuous visibility into your entire cloud environment, with configuration management, runtime security, and cyber threat detection. For distributed teams, centralized visibility is crucial. Security teams need a single pane of glass to understand what is running and the cybersecurity risks involved when developers across time zones independently deploy a service.
Endpoint Detection and Response
Traditional antivirus software does an adequate job of detecting known malware through signature comparison, but it will fall short against modern targeted attacks. Endpoint Detection and Response (EDR) agents continuously monitor device activity, including which processes are initiated, which files are opened, and which network connections are established. They leverage behavior analysis to identify cybersecurity threats early before they can wreak havoc. Use cloud-based EDRs that can be centrally managed and do not utilize a VPN. To strengthen device-level monitoring for distributed teams, consider how extended detection and response (XDR) complements EDR by correlating telemetry across endpoints, identity, email, and cloud services to detect lateral movement and automate response. For a practical XDR and EDR security comparison that clarifies where EDR falls short and when XDR is the better fit, review this concise breakdown.
Zero-Trust Network Access
Assume that whenever employees access internal applications from networks you do not control, someone may be watching that traffic. Zero-trust security replaces the legacy VPN model with application-level inspection. Inspections verify user identity, device health, and other factors before granting access to targeted resources. The increased level of control will significantly reduce attackers' ability to move laterally if they access a single account. Zero-Trust secures internal apps, but remote teams still use public networks. Pair it with a modern VPN to encrypt traffic on untrusted Wi-Fi and reduce tracking, without slowing SaaS access. Prioritize one-click connect, strong encryption, a kill switch, and split tunneling.
Establishing Scalable Cybersecurity Awareness
Technology and cybersecurity policy lay the foundation, but culture determines whether security is effective in practice.
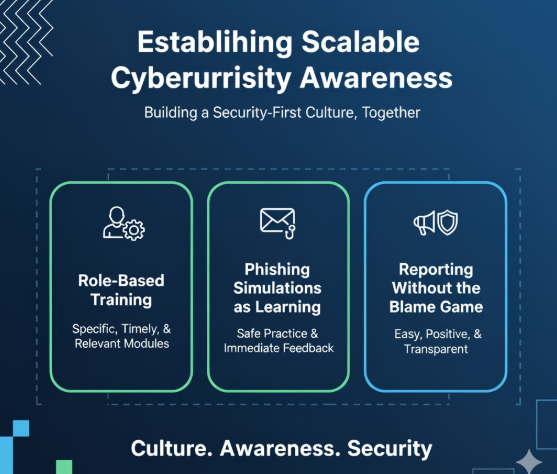
Role-Based Training
Generic cybersecurity training is ineffective because it is situated far from real work. For instance, Virtual Assistants who manage an executive’s calendar need training focused on executive impersonation scams. Engineers need training most pertinent to their positions on secure coding or secrets management. Finance staff need training on verifying wire transfers. The most effective training is brief, specific education delivered in 15-minute monthly modules, rather than once-a-year employee training that may last several hours.
Phishing Simulations as Learning
Regularly run phishing simulation attacks for your users to make the concept of an abstract threat actionable. Begin with simple simulations to build confidence, then run full-blown simulations similar to the range of attacks users encounter. The response to a click is critical: do not punish, but offer immediate feedback that targets the suspicious item and demonstrates that a similar message is being reported in the case of a real phishing email.
Reporting Without the Blame Game
Even the best security tools will not help if your employees are afraid to report. Create simple capabilities for employees to report suspected attack-related issues. Act quickly and positively, and provide timely feedback, even in false-alarm cases. Make data breaches and suspicious messages visible, and have leaders share them, as this will lead to similar responses from the general population.
Make Security Your Strategic Advantage
Security does not hinder distributed teams. Instead, it fosters the speed and trust needed to effectively scale remote work with a distributed workforce. Organizations that adopt security from the outset, combining policies and automated controls with a strong culture, can tap into a global workforce without the security threats that impede their competitors.
This article provides a simple framework.
Five policies to set clear, consistent expectations; five technologies to facilitate compliance; training tailored to each role; and access management that scales with your team. When everyone clearly understands their role in security and has access to the appropriate tools, security becomes a foundation for sustainable remote work.